Introduction
In the world of bitcoin, transactions are irrevocable, and once coins are stolen, they cannot be recovered. This makes wallet security paramount. Since launching bitcoin support, we have developed a robust approach to bitcoin cold storage and recognize the importance of sharing our work with the community. In this blog post, we present a research attack on bitcoin custody.
To safeguard funds and prevent theft, it’s essential for us to think offensively—to consider how best to break the system in order to understand its weaknesses. In 2021, we developed a novel attack that stealthily leaks private seeds when users sign transactions, all without detection. This method operates covertly, ensuring that the user remains unaware while their sensitive data is exfiltrated during routine signing operations, highlighting the critical need for proactive security measures.
Our paper was later accepted at the 18th USENIX Workshop on Offensive Technologies. This attack is a very efficient and practical method for compromising air-gapped wallets. The attack imposes minimal overhead on regular signing operations, making it particularly practical. It also works in real-world conditions, tolerating scenarios like missing signatures or transaction reordering, without compromising its effectiveness.
The Attack
In this section, we provide a brief overview of the key aspects of the attack. For a complete technical analysis, you can read our full paper here.
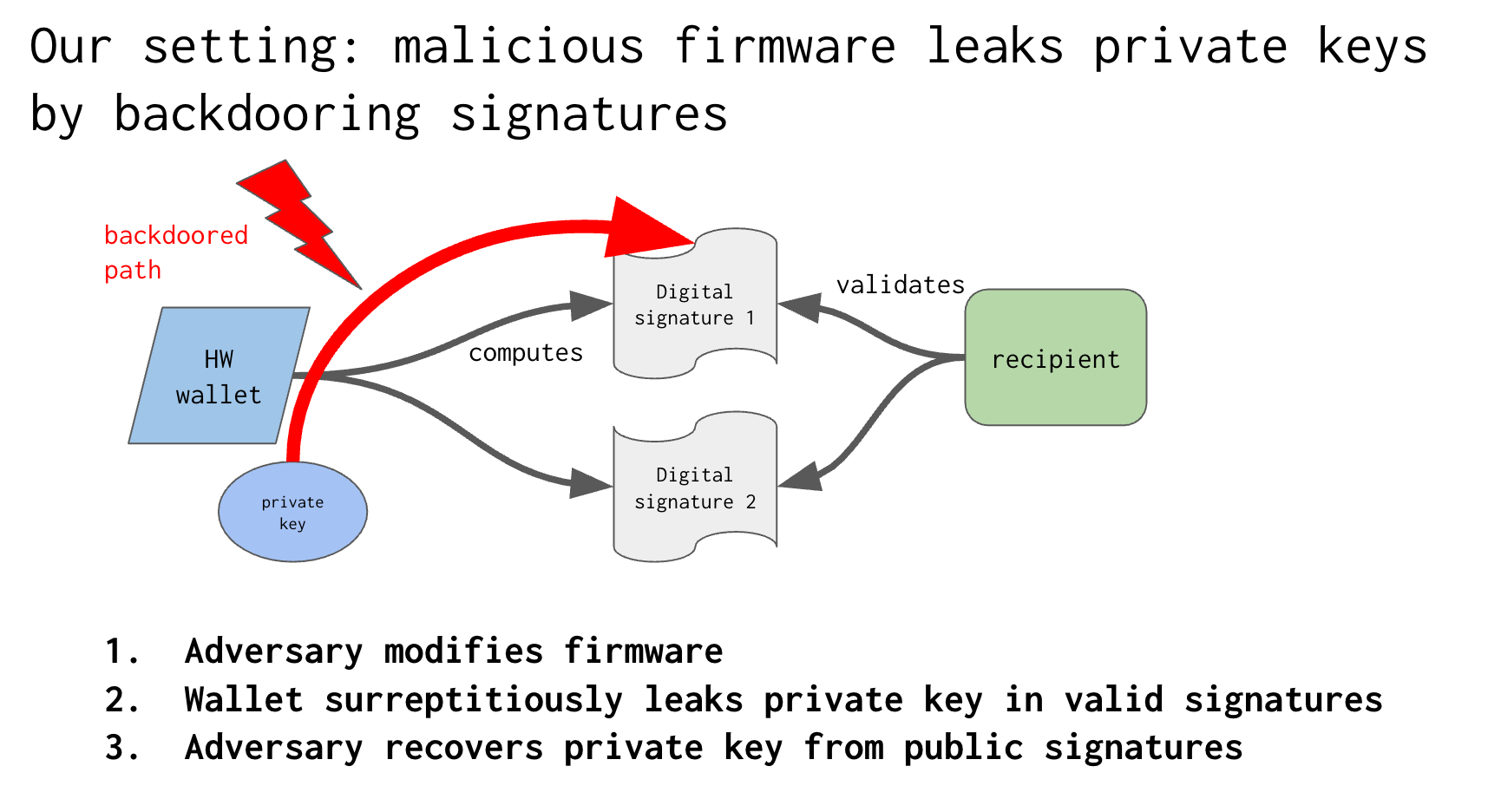
Threat model: This attack operates under a powerful threat model, where an adversary gains full control over the hardware wallet’s firmware. While this might seem extreme, there are multiple realistic vectors for such an attack, including supply-chain compromises, insider threats, breaches in the build system, or the compromise of firmware signing keys. These attack paths, although difficult, are not impossible and must be hardened against.
How the attack works: At a high level, this attack works by cooking the randomness used in Bitcoin’s digital signature algorithms, such as ECDSA or Schnorr. Using a secure, random nonce is essential to maintaining the security of ECDSA and Schnorr signatures. In a compromised hardware wallet, nonces could be manipulated to appear random but actually contain parts of the private keys. Over time, with a small number of signatures, an attacker could reconstruct the entire long term private key. Our attack embeds parts of the master secret key into the randomness of the signature process, using erasure codes to distribute these fragments in a robust way. This technique was already started by Simmons, we improve it to handle full-size seeds (about 256 bits) and tolerate missing or reordered signatures.
How Does It Compare?
We developed this attack independently from another exfiltration technique, Dark Skippy. The attack presented here serves as a generalization of Dark Skippy, making it adaptable to broader, real-world conditions. Unlike Dark Skippy, which requires a specific transaction structure with two inputs, our method operates without such constraints. Our technique is designed to handle the possibility that the sequence of signed transactions may differ from the order in which they are broadcast or mined. It’s also robust in situations where some signed transactions may never be broadcast or might fail. Our code and benchmarks, which demonstrate the attack’s effectiveness and practicality, will be shortly available on GitHub.
Mitigations and Lessons
The most effective way to defend against backdoors is to eliminate single points of failure and prevent initial firmware compromise. One straightforward approach is to split trust across multiple systems, a capability that Bitcoin supports at the protocol level with multi-signatures. Our focus on Bitcoin allows us to fully leverage its native protocol features. While other exchanges implement complex and error-prone systems like multi-party computation (MPC) to accommodate multiple cryptocurrencies, we rely on Bitcoin’s built-in features, which are more robust, easier to implement, and specifically designed for Bitcoin’s security needs. This attack class can be carried out by compromising the software supply chain. At Block, we use deterministic builds, ensuring that anyone can reproduce and verify our cold wallet software integrity. This greatly reduces the risk of supply chain attacks by guaranteeing that the deployed software matches the original source. Additionally, we bolster security with build diversity—using multiple builders, offline builds, and strict dependency pinning—further reducing vulnerabilities and making it much harder for any single point in the process to be compromised. You can read more about Subzero’s security design in the full blog here.
Bitkey: Hardware Wallet Security
We apply similar principles to Bitkey, our hardware wallet. Bitkey uses a 2-of-3 multisig setup, splitting trust between Block’s servers, the customer’s phone, and the hardware device. The Bitkey hardware features secure boot on its main microcontroller (SiLab’s EFR32MG24), which means that it will only execute authentic firmware. Each Bitkey firmware also carries unique attestation certificates to ensure that only authentic devices interact with the Bitkey app. This protects against counterfeit, malicious hardware, or supply-chain attacks. This raises the attack cost and makes Bitkey highly resistant to stealthy exfiltration attacks.
Final Thoughts
Bitcoin lets us remove trusted third parties, but it doesn’t eliminate the need for trust altogether — it just moves it deeper into the stack. That trust now lives in firmware, hardware, and the processes that govern them. Our work focuses on shrinking that trust footprint as much as possible, through secure design, transparency, and rigorous testing. If you're passionate about tackling these challenges and interested in building more secure systems, we’re hiring. Reach out to us at bitcoin-hiring@squareup.com.